4.6.4 Certificates
Some 2N® LiftIP 2.0 network services use the secure TLS protocol for communication with the other LAN devices. This protocol prevents third parties from eavesdropping or modifying call contents. TLS communication is based on one/two-sided authentication, which requires certificates and private keys.
Device services that use the TLS protocol:
- Web server (HTTPS)
- SIPs
2N® LiftIP 2.0 allows you to upload sets of CA certificates, which are used for identity verification of the communicating device, and upload user certificates and private keys used for communication encryption.
Each certificate requiring service can be assigned one certificate set, refer to the Web Server subsection. The certificates can be shared by the services.
- 2N® LiftIP 2.0 accepts certificates in the DER (ASN1) and PEM formats.
- 2N® LiftIP 2.0 supports the AES, DES and 3DES encryption standards.
- 2N® LiftIP 2.0 supports the following algorithms:
- RSA up to 2048bit key size for user uploaded certificates; internally up to 4096bit keys (while connection – intermediate and equivalent certificates)
- Elliptic Curves
Caution
- The CA certificates must use the X.509 v3 format.
Upon the first power supply connection, the so-called Self Signed certificate and private key are generated to be used for the Web server and E-mail services without the need to upload a certificate and private key of your own.
Note
- In case you use the Self Signed certificate for communication encryption between the device web server and the browser, your communication is secure, but you will be warned by the browser that the intercom certificate’s trustworthiness cannot be verified.
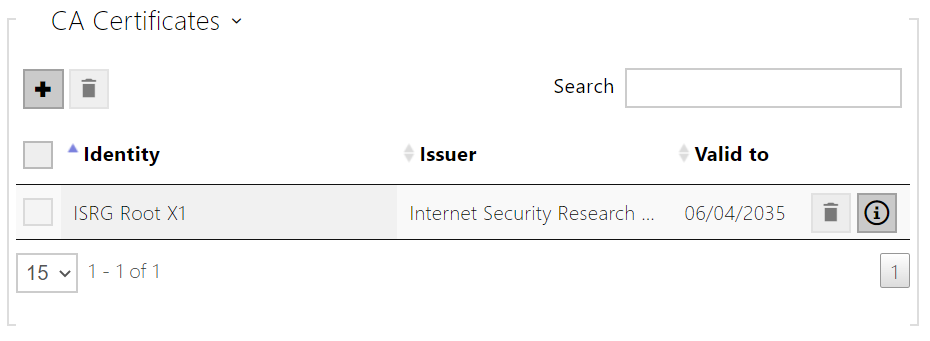
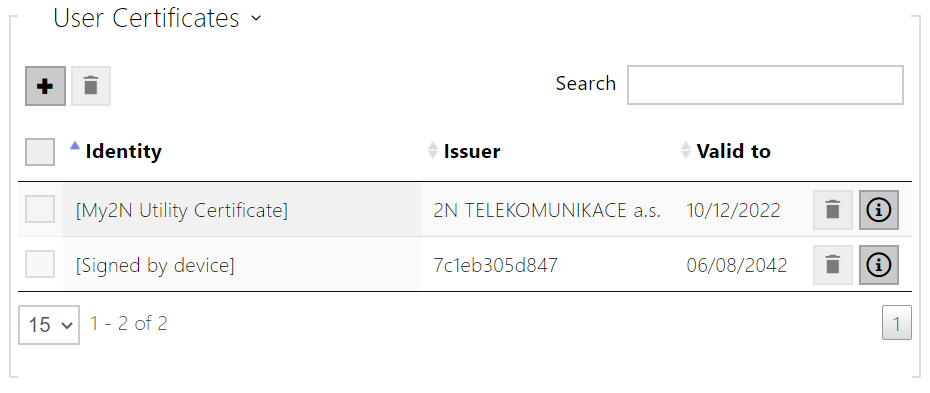
The current list of uploaded CA certificates and user certificates is displayed in two folders:
Click to upload a certificate saved on your PC into the device. Select the certificate (or private key) file in the dialog box and click Upload. Press to remove the certificate. Press to show certificate information.
Caution
- Note that a certificate with a private RSA key longer than 2048 bits may be rejected. In that case, the following message will be displayed: The private key file/password was not accepted by the device!
- For certificates based on elliptic curves use the secp256r1 (aka prime256v1 aka NIST P-256) and secp384r1 (aka NIST P-384) curves only.