3.2.6 Firewall
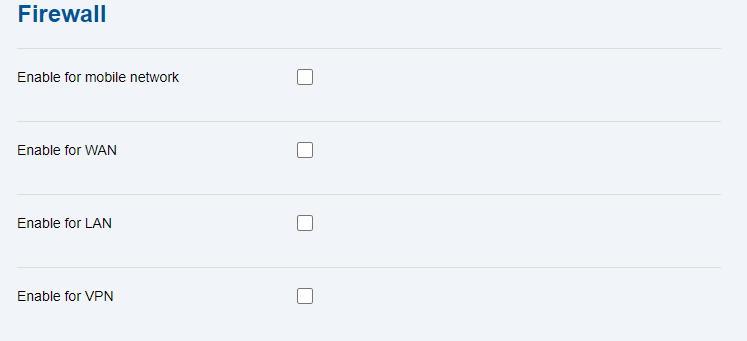
The Firewall tab is used for setting access to 2N LiftGate from a selected network. If the firewall is inactive, there are no restrictions for the given network; if it is active, only the accesses defined in the table below are allowed.
- Enable for mobile network (MN) – allow access of firewall from a mobile network.
- Enable for WAN – allow access of firewall from a WAN port.
- Enable for LAN – allow access of firewall from a LAN port.
- Enable for VPN – allow access of firewall from a VPN.
Caution
- Receiving incoming ICMP and ICMPv6 packets is not restricted by enabling the firewall.
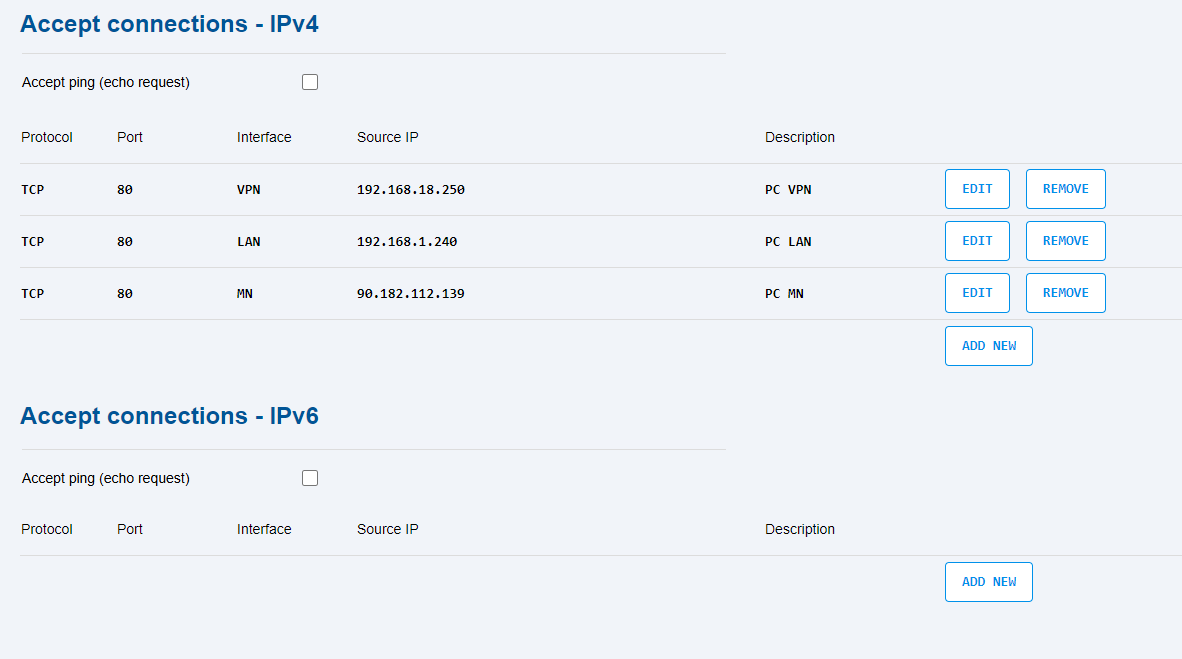
- Accept ping (echo request) – enable accepting incoming PING requests. The selection is applied in the given interface only if the firewall for the given interface is on.
The Accept connection table includes the allowed accesses from the Internet.
- Protocol – TCP or UDP.
- Port – port number (0 to 65535).
- Interface – for selected connection (MN, WAN, LAN, VPN) or any.
- Source IP – for a remote device with this address, or with any address if the parameter is empty.
- Description – user definable field for a connection.
- ADD NEW – add a new connection.
Caution
- If the firewall is active and access should be allowed to the device web interface from the selected network, the TCP and port 80 (HTTP) or 443 (HTTPS) should be enabled.
- Enabling the LAN firewall will limit the proper functioning of the DNS and DHCP servers. To maintain their correct function, it is necessary to enable their connection.
| Port | Service | Protocol | Interface |
|---|---|---|---|
| 53 | DNS server | UDP | LAN |
| 67 | DHCP server | UDP | LAN, VPN |
| 68 | DHCP client | UDP | MN, VPN, WAN, |
| 80 | HTTP server | TCP | LAN, MN, VPN, WAN |
| 443 | HTTPS server | TCP | LAN, VPN, MN, WAN |
| 546 | DHCPv6 client | UDP | VPN, WAN |
| 547 | DHCPv6 server | UDP | LAN |