5.4.1 Access Control
Access Control helps you manage accesses and verify user authentications.
Entry Rules
- Access Enabled – enable access in a direction (entry, exit). If access is disabled, the door cannot be opened from the selected side.
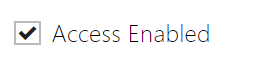
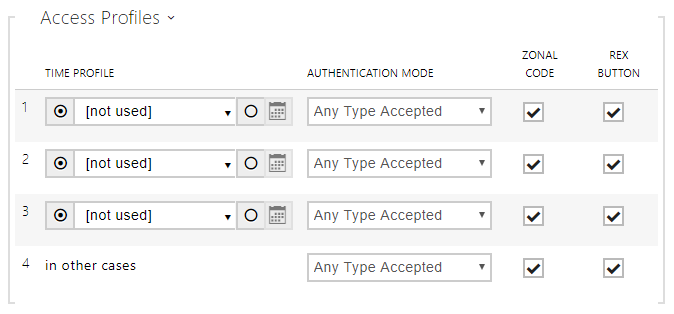
- Time Profile – choose one or more time profiles to be applied. Set the time profiles in Directory > Time profiles.
- – select global profiles from Directory > Time Profiles.
- – individual time profile for this specific element.
- – select global profiles from Directory > Time Profiles.
- Authentication Mode – set the authentication mode for the time profile in this row including multiple authentication for enhanced security. Select Access denied to ban access.
- Zonal Code – enable the zonal code for the time profile and authentication combination in this row. You can use the zonal code instead of the user PIN.
Caution
- If the time profile is unset, the authentication mode is ignored on the given row.
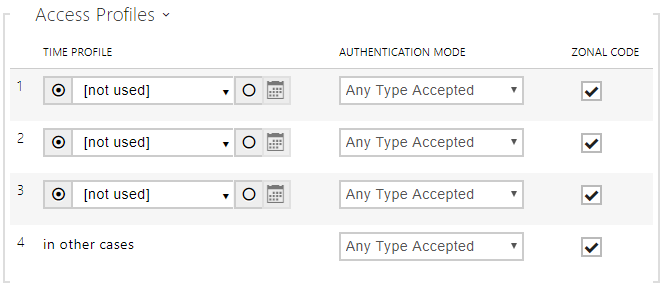
- Access Blocking – display the active Access Blocking setting: ON/OFF.
- Zonal Code – enter the switch numeric zonal code consisting of two characters at least. However, four characters at least are recommended.
- Virtual Card to Wiegand – select a group of Wiegand outputs to which the Virtual user card No. shall be sent after successful authentication. Can be combined with any authentication method, including codes, fingerprints, etc.
- Silent Alarm Enabled – a virtual code higher by 1 than the access code is assigned to each access code and used for silent alarm activation. For example, if the access code is 0000, then the silent alarm activation code is 0001. It means, for instance, that silent alarm is 0000 for access code 9999 and so on. Set the silent alarm action in the Automation section.
Caution
- In case the user authenticates itself and activates the silent alarm that is deactivated, the user access will be denied and the alarm will not be activated.
- Limit Failed Access Attempts – enable the maximum count of unsuccessful authentication attempts. After five unsuccessful attempts (wrong numeric code, invalid card, etc.), the 2N access control unit will be blocked for 30 seconds even if authentication is valid.
- License Plate Recognition Enabled – Enables license plates to be used as an access credential.
- License Plate Recognition Mode – Choose the scenario after the license plate is recognized. Refer to the manual for function details.
The device allows you to use the recognized license plates sent in an HTTP request by the AXIS cameras equipped with an optional application VaxALPR on api/lpr/licenseplate (refer to the HTTP API Manual for IP Intercoms).
In case the function is on, the event is recorded into the LicensePlateRecognized history when a valid HTTP request has been received. If an image is sent within the HTTP request (photo part or whole photo of the license plate detecting scene), it is saved. The last five photos are stored in the device memory and can be retrieved via an HTTP request sent to api/lpr/image available in 2N Access Commander.
Warning
- The software factory reset or different configuration upload does not result in a change of the access blocking setting. It is only the hardware factory reset using the Reset button on the device that resets the default values.
- The Security Relay enhances the installation security against hardware reset misuse.
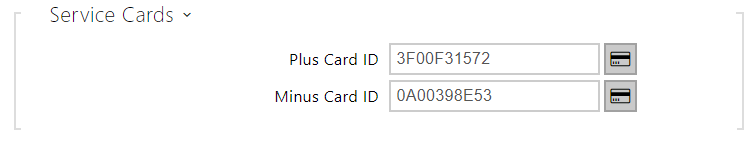
- Plus Card ID – enter the service card ID for adding cards to the Installed cards: a sequence of 6 to 32 characters including 0–9, A–F.
- Minus Card ID – enter the service card ID for removing cards from the Installed cards: a sequence of 6 to 32 characters including 0–9, A–F.
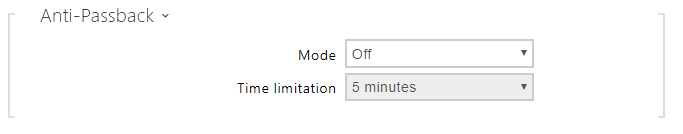
- Mode – enable/disable the Anti-Passback mode:
- Off – the function is Off by default allowing the user to use the access card or another identifier to re-enter an area without leaving it before.
- Soft – the user is allowed to use the access card or another identifier to re-enter an area without leaving it before. A new UserAuthenticated record with apbBroken=true will be created in the Status > Events section.
- Hard – the user is not allowed to use the access card or another identifier to re-enter an area without leaving it before. A new UserAuthenticated record with apbBroken=true will be created in the Status > Events section.
- Time Limitation – select an Anti-Passback timeout during which the user cannot re-enter an area using the given authentication method (card, code, etc.) in the same direction.
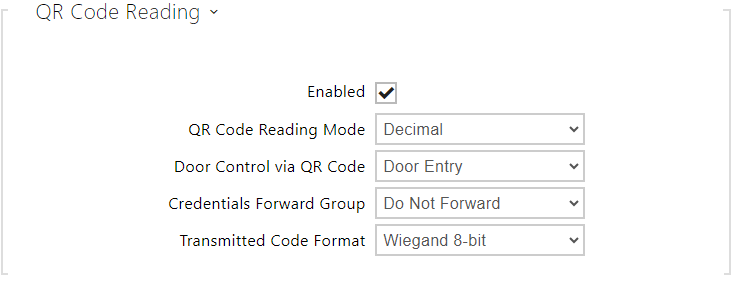
- Enabled – enable/disable QR code reading using the device camera. If QR code reading is enabled, it is possible to enter PIN codes and individual switch codes longer than ten digits by showing the QR code to the device camera.
- QR Code Reading Mode – the device always stores decimal codes. In Decimal mode, the scanned codes must match the 4 to 15-digit codes stored in the device. In Hexadecimal mode, the codes are converted to decimal after scanning and compared with the stored decimal codes, disregarding any leading zeroes. Accepted hexadecimal range: 1000 to FFFFFFFF.
- Door Control via QR Code – Enables or disables door control by reading a QR code.
- Credentials Forward Group – set the group to which all entered access codes will be forwarded.
- Transmitted Code Format – selects a 4bit or 8bit (higher security) format for the codes to be transmitted
Caution
- Do not use privacy masking in combination with QR code reading to make the QR code reading function work properly.
For increased security, limit the count of unsuccessful accesses in the Advanced Settings block above.
- The QR code reading function is only available in models equipped with the ARTPEC-7 microcontroller supplied by Axis.
Exit Rules
- Access enabled – enable access in a direction (entry, exit). If access is disabled, the door cannot be opened from the selected side.
- Time Profile – choose one or more time profiles to be applied. Set the time profiles in Directory > Time profiles.
- – select one of the pre-defined profiles or set the time profile for the given element manually.
- Authentication Mode – set the authentication mode for the time profile in this row including multiple authentication for enhanced security. Select Access denied to ban access.
- Zonal Code – enable the zonal code for the time profile and authentication combination in this row. You can use the zonal code instead of the user PIN.
- REX Button – enable the exit button function for the selected time profile. Set the exit button input in Hardware > Door > Door tab.
Caution
- If the time profile is unset, the authentication mode is ignored on the given row.
- Access Blocking – display the active Access Blocking setting: ON/OFF.
- Zonal Code – enter the switch numeric zonal code consisting of two characters at least. However, four characters at least are recommended.
- Virtual Card to Wiegand – select a group of Wiegand outputs to which the Virtual user card No. shall be sent after successful authentication. Can be combined with any authentication method, including codes, fingerprints, etc.
- Silent Alarm Enabled – a virtual code higher by 1 than the access code is assigned to each access code and used for silent alarm activation. For example, if the access code is 0000, then the silent alarm activation code is 0001. It means, for instance, that silent alarm is 0000 for access code 9999 and so on. Set the silent alarm action in the Automation section.
Caution
- In case the user authenticates itself and activates the silent alarm that is deactivated, the user access will be denied and the alarm will not be activated.
- Limit Failed Access Attempts – enable the maximum count of unsuccessful authentication attempts. After five unsuccessful attempts (wrong numeric code, invalid card, etc.), 2N access control unit will be blocked for 30 seconds even if authentication is valid.
- License Plate Recognition Enabled – Enables license plates to be used as an access credential.
- License Plate Recognition Mode – Choose the scenario after the license plate is recognized. Refer to the manual for function details.
The device allows you to use the recognized license plates sent in an HTTP request by the AXIS cameras equipped with an optional application VaxALPR on api/lpr/licenseplate (refer to the HTTP API Manual for IP Intercoms).
In case the function is on, the event is recorded into the LicensePlateRecognized history when a valid HTTP request has been received. If an image is sent within the HTTP request (photo part or whole photo of the license plate detecting scene), it is saved. The last five photos are stored in the device memory and can be retrieved via an HTTP request sent to api/lpr/image available in 2N Access Commander.
Warning
- The software factory reset or different configuration upload does not result in a change of the access blocking setting. It is only the hardware factory reset using the Reset button on the device that resets the default values.
- The Security Relay enhances the installation security against hardware reset misuse.
- Plus Card ID – enter the service card ID for adding cards to the Installed cards: a sequence of 6 to 32 characters including 0–9, A–F.
- Minus Card ID – enter the service card ID for removing cards from the Installed cards: a sequence of 6 to 32 characters including 0–9, A–F.
- Mode – enable/disable the Anti-Passback mode:
- Off – the function is Off by default allowing the user to use the access card or another identifier to re-enter an area without leaving it before.
- Soft – the user is allowed to use the access card or another identifier to re-enter an area without leaving it before. A new UserAuthenticated record with apbBroken=true will be created in the Status > Events section.
- Hard – the user is not allowed to use the access card or another identifier to re-enter an area without leaving it before. A new UserAuthenticated record with apbBroken=true will be created in the Status > Events section.
- Time Limitation – select an Anti-Passback timeout during which the user cannot re-enter an area using the given authentication method (card, code, etc.) in the same direction.
Secure Cards
- MIFARE DESFire Keys – indicates the state of the configuration for MIFARE DESFire cards reading. If any of the MIFARE DESFire reading parameters is missing or invalid in the configuration, the state is Not configured. If all the parameters are present and valid, the state is Configured.
- Hash – project numerical ID.
- Delete Keys – delete the uploaded MIFARE DESFire keys.
Caution
- If you use the MIFARE DESFire cards, remember to disable reading of insecure CSNs. Enable the cards in the card reader settings in Hardware > Extending modules.
MIFARE DESFire Card Configuration
- Get ready the MIFARE DESFire card values for access control management.
Create an XML file with the below-mentioned structure (example of an XML structure).
Keep the length and format of the values. If your data value is shorter than the required count of characters, add initial zeros from the left. Enter the values without the hexadecimal prefix.
- Upload the XML file to the device via System > Maintenance > Configuration > Upload configuration file.
- Once the XML file has been uploaded, the device restores the configuration. The code segment will be included in the complete configuration file of the device.
<DeviceDatabase>
<CardReader>
<KeyStore>
<Keys>
<Desfire>
<AID>130586</AID>
<KeyNo>01</KeyNo>
<AuthKey>B52874F4E3EEE03C349EBB74A3123458</AuthKey>
<KeyType>01</KeyType>
<AuthMode>01</AuthMode>
<FileNo>01</FileNo>
<Offset>000000</Offset>
<Bits>00000080</Bits>
<DecodeASCII>01</DecodeASCII>
</Desfire>
</Keys>
</KeyStore>
</CardReader>
</DeviceDatabase>
| Key | Value type/format | Description |
|---|---|---|
| AID | 6 hexadecimal chars | Application Identifier (AID): Unique app identifier on a MIFARE DESFire card. Every card can include multiple applications and each app has files and keys of its own. |
| AuthKey | 32 hexadecimal chars | Authentication Key: Cryptographic key (AES 128) used for secure authentication and encrypted communication setup on the card. |
| KeyType | 01 (including initial zeros) | Key Type: Define the encryption algorithm used. At present, AES 128 is only supported, for which the value 01 is entered. |
| AuthMode | 00: No authentication01: AES authentication | Authentication Mode: Enable/disable authentication using AuthKey. Set 01 for secure access to the files. |
| FileNo | 00 to 1F | File Number: Identifier of a specific data file within a selected application (AID). There can be up to 32 files in one application. |
| Offset | 6 hexadecimal chars | Offset: Set the initial position (in bytes) from which the file data should be read. The value 000000 indicates the file beginning. |
| Bits | 8 hexadecimal chars | Bits: Define how many bits are to be read from the file (starting from the O |
| DecodeASCII |
| Decoding to ASCII: Define whether or not the binary data read from the card shall be automatically interpreted and decoded as text characters in the ASCII format. |
Caution
No card reader for 2N Electronic Lock cards reading is connected or paired.
- 2N Electronic Lock Keys – indicates the state of the configuration for Electronic Lock keys reading. If any of the Electronic Lock reading parameters is missing or invalid in the configuration, the state is Not configured. If all the parameters are present and valid, the state is Configured.
- Hash – project numerical ID.
- Delete Keys – delete the uploaded Electronic Lock keys.
Caution
- Refer to the 2N PICard Commander Configuration Manual for the devices on which cards with the PICard technology can be read.
- Description – encryption key name.
- Hash – project numerical ID.
- PICard Keys
- Delete – delete the uploaded PICard keys.
- Upload – select the key file and enter the valid password to upload the PICard key.
WaveKey
The 2N devices equipped with the Bluetooth module allow for user authentication via the My2N application available to devices with iOS 12 and higher (iPhone 4s and higher phones) or Android 6.0 Marshmallow and higher (Bluetooth 4.0 Smart supporting phones).
User Identification (Auth ID)
The My2N application authenticates itself with a unique identifier on the 2N device side: Auth ID (128-bit number) is generated randomly for every user and paired with the intercom user and its mobile device.
Note
- The generated Auth ID cannot be saved in more mobile devices than one. This means that Auth ID uniquely identifies just one mobile device or its user.
You can set and edit the Auth ID value for each user in the Mobile Key section of the device Users list. You can move Auth ID to another user or copy it to another device. By deleting the Auth ID value you can block the user's access.
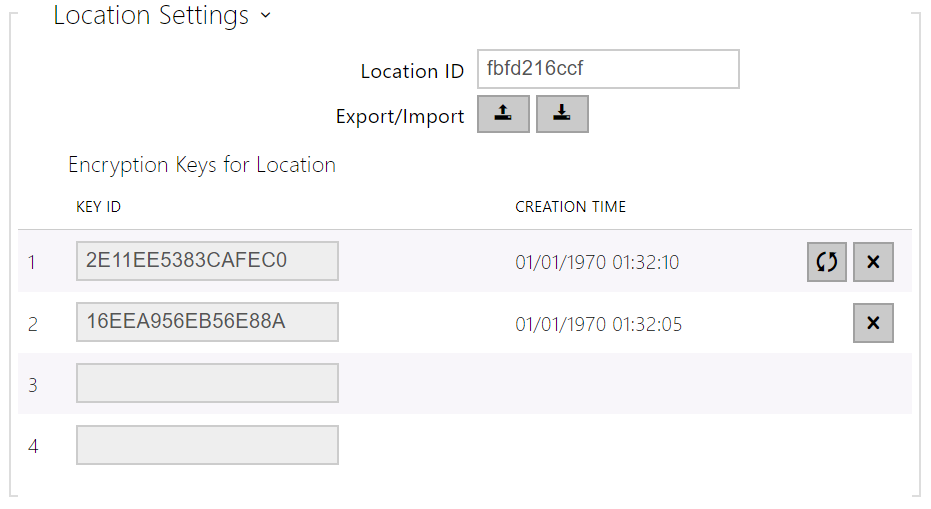
Encryption Keys and Locations
The My2N – device communication is always encrypted. WaveKey cannot authenticate a user without knowing the encryption key. The primary encryption key is automatically generated upon the device first launch and can be re-generated manually any time later. Together with AuthID, the primary encryption key is transmitted to the mobile device for pairing.
You can export/import the encryption keys and location identifier to other devices. The 2N devices with identical location names and encryption keys form so-called locations. In one location, a mobile device is paired just once and identifies itself with one unique Auth ID (i.e. a user AuthID can be copied from one intercom to another within a location).
Pairing
Pairing means transmission of user access data to a user personal mobile device. The user access data can only be saved into one mobile device, i.e. a user cannot have two mobile devices for authentication, for example. However, the user access data can be saved into multiple locations in one mobile device (i.e. the mobile device is used as a key for more locations at the same time).
To pair a user with a mobile device, use the user's page in the device Users list. Physically, you can pair a user locally using the USB Bluetooth module connected to your PC or remotely using an integrated Bluetooth module. The results of both the pairing methods are the same.
The following data is transmitted to a mobile device for pairing:
- Location identifier
- Location encryption key
- User Auth ID
Encryption Key for Pairing
An encryption key other than that used for communication after pairing is used in the pairing mode for security reasons. This key is generated automatically upon the intercom first launch and can be re-generated any time later.
Encryption Key Administration
The 2N device can keep up to 4 valid encryption keys: 1 primary and up to 3 secondary ones. A mobile device can use any of the 4 keys for communication encryption. The encryption keys are fully controlled by the system administrator. It is recommended that the encryption keys should be periodically updated for security reasons, especially in the event of a mobile device loss or 2N device configuration leak.
Note
- The encryption keys are generated automatically upon the 2N device first launch and saved into its configuration file. We recommend you to re-generate the encryption keys manually before the first use to enhance security.
The primary key can be re-generated any time. Thus, the original primary key becomes the first secondary key, the first secondary key becomes the second secondary key and so on. Secondary keys can be deleted any time.
When a key is deleted, the WaveKey users that still use this key will not be able to authenticate themselves unless they have updated the encryption keys in their mobile devices before deletion. The mobile device keys are updated at every use of the My2N application.
List of Parameters
- Location ID – set a unique identifier for the location in which the selected encryption key set is valid.
- Export – push the button to export the location ID and current encryption keys into a file. Subsequently, the exported file can be imported to another device.
- Import – push the button to import the location ID and current encryption keys from a file exported from another device.
- Restore primary key – by generating a new primary encryption key you delete the oldest secondary key. Thus, the WaveKey users that still use this key will not be able to authenticate themselves unless they have updated the encryption keys in their mobile devices before deletion. The mobile device keys are updated at every use of the 2N My2N application.
- Delete primary key – delete the primary key to prevent the users that still use this key from authentication.
- Delete secondary key – the 2N My2N users that still use this key will not be able to authenticate themselves unless they have updated the encryption keys in their mobile devices before deletion. The mobile device keys are updated at every use of the My2N application.
- Pairing PIN validity – set the authorisation PIN validity for user mobile device pairing with the 2N device.
Tip
- In the case of loss of a mobile phone with access data proceed as follows:
- Delete the Mobile Key Auth ID value for the user to block the lost phone and avoid misuse.
- Re-generate the primary encryption key (optionally) to avoid misuse of the encryption key stored in the mobile device.
Warning
- With the upgrade to version 2.30, the bluetooth modules will also be upgraded. When downgrading to version 2.29 and lower, they may malfunction.
- Compatibility Mode – ensures the WaveKey function for those users who cannot update to My2N 3.5.0 (Android) or 3.7.0 (iOS) and higher. Once the Compatibility mode is deactivated, the primary key has to be generated again.
Note
Update to My2N 3.5.0 (Android) or 3.7.0 (iOS) and higher
- Make sure that all the users have installed a new version of the My2N application.
- Install firmware version 2.47 or higher on the device.
- Deactivate the Compatibility mode.
- Generate a new primary key.
OSDP
The OSDP provides secure communication for sending such login data as access card IDs or PIN codes between the connected OSDP device (control panel, door controller) and the 2N acces control units. The goal is to enable signaling on the device based on the counterparty's response to the card signaling definition sent.
- OSDP Signaling Enable – definition string for access enable signaling.
- OSDP Denied Signaling – definition string for access denial signaling.
Note
- If identical definitions are inserted in the two parameters above, an evaluation is made with audio visual signals as if one authorized access and one unauthorized access have been used closely one after another.
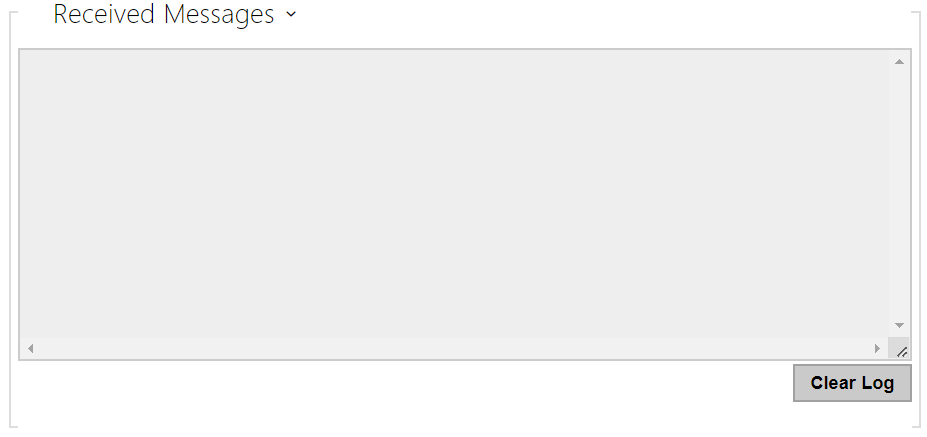
The Received Messages box helps you get the definition string. When an access card is tapped on the device reader, the counterparty's OSDP signaling definition is displayed for authorized / unauthorized access.
The received message is displayed in the following format:
13:46:39] led(0,0,0,0,0,0,0,0,1,1,1,2,2)
13:46:39] buz(0,2,1,1,1)
13:46:42] led(0,0,0,0,0,0,0,0,1,1,1,1,1)
13:46:42] buz(0,1,0,0,0)
A part of the message (without the time value) is used as the definition string, whose length may not exceed 255 characters, e.g.: led(0,0,0,0,0,0,0,0,1,1,1,1,1) or buz(0,2,1,1,1). Having evaluated a match on the counterparty, the device responds with an adequate signaling. Any part of the definition can be replaced with "*", which will be interpreted as an arbitrary message content (e.g. it is possible to ensure that signaling will be activated upon any LED 0 light on the device regardless of the other message parameters).
- Clear Log – delete a Received messages record.
Note
- Make sure that the Door / Unused parameter is set for the card reader and keypad in Hardware > Extending modules to make the function work. The 2N device confirms the card reading by a beep and the device responds with an appropriate signaling after evaluation.
Integration with Other Systems
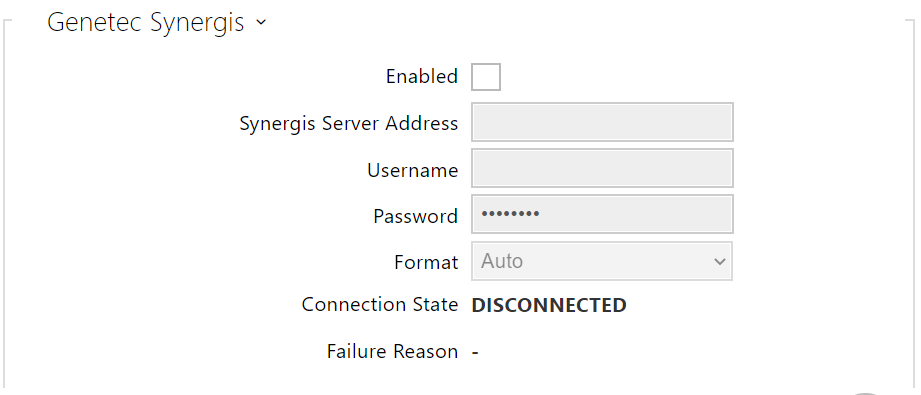
- Enabled – enable connection with the Genetec Synergis external security system.
- Synergis Server Address – Synergis server IP address or domain name.
- Username – authentication user name.
- Password – authentication password.
- Format – set the card reading format for sending card IDs to Genetec Synergis.
- Forward Code – set whether or not the set codes are to be resent. The codes may contain up to 6 digits and their ends have to be confirmed with a key.
- Connection State – display the current Synergis server connection state or error state description if necessary.
- Failure Reason – display the failure reason of the last Synergis server connection attempt – the last error response, 404 Not Found, for example.
Advanced Folder
- Character Trimming Direction – choose whether trimming of recognized license plates is permitted, and specify the direction from which trimming may be attempted.
- Maximum Characters to Trim – choose the maximum number of characters to trim, either 1 or 2. Trimming occurs at the beginning or end of the string based on the selected Character Trimming Direction.
- Interchangeable Characters – define interchangeable character pairs for the purposes of the License Plate Recognition function. The first character in a pair will be replaced with the second character for the purposes of matching saved license plates. A dash separates the characters in a pair. Multiple pairs can be entered and separated by a comma. Whitespace is ignored. Example:<br>O-0, I-1<br><br>.
- Compatibility Mode – support older card reading modes. This mode is not recommended in combination with the PICard cards. If this mode is off, the card numbers must be a perfect match for successful authorization.
- Remove Invalid Users Delay – set the delay after which users with invalid access and enabled automatic removal are removed from the device directory.