5.5.6 Auto Provisioning
2N access control units allow you to update firmware and configuration manually or automatically from a storage on a TFTP/HTTP server selected by you according to predefined rules.
You can configure the TFTP and HTTP server address manually. The 2N device supports automatic address identification via the local DHCP server (Option 66).
Caution
- The login password is saved in the configuration file. If the password is 2n (default), the valid configuration part is only uploaded. This means that the configuration is uploaded, but the password remains the same, not assuming the value included in the file.
My2N
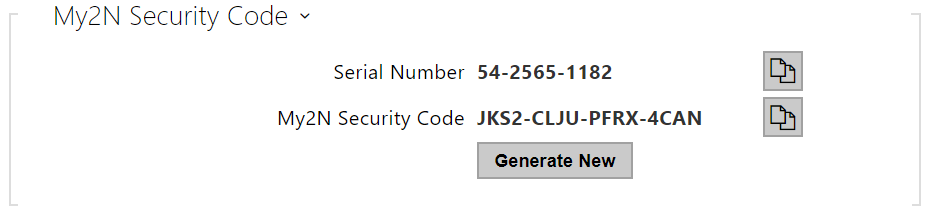
- Serial Number – display the serial number of the device to which the valid My2N code applies.
- My2N Security Code – display the full application activating code.
- GENERATE NEW – the active My2N Security Code will be invalidated and a new one will be generated.
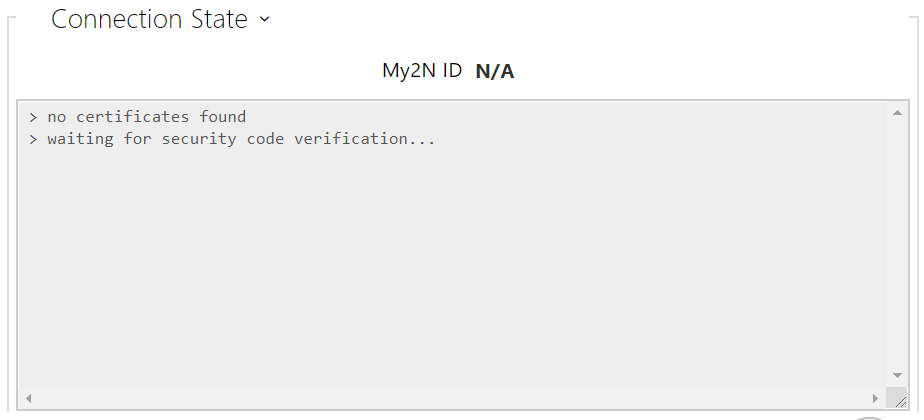
- My2N ID – unique identifier of the company created via the My2N portal.
Firmware
Use the Firmware tab to set automatic firmware download from a server defined by you. The device compares the server file with its current firmware file periodically and, if the server file is more recent, automatically updates firmware and gets restarted (approx. 30 s). Hence, we recommend you to update when the device traffic is very low (at night, e.g.).
The 2N access control units expect the following files:
- MODEL-firmware.bin – device firmware
- MODEL-common.xml – common configuration for all devices
- MODEL-MACADDR.xml –specific configuration for one device
MODEL in the filename specifies the device model:
- au – 2N Access Unit
- aug2 – 2N Access Unit 2.0
- aum – 2N Access Unit M
- auqr - 2N Access Unit QR
MACADDR is the MAC address of the device in the 00-00-00-00-00-00 format. Find the MAC address on the device production plate or on the Status tab in the web interface.
Example:
2N Access Unit 2.0 with MAC address 00-87-12-AA-00-11 downloads the following files from the TFTP server:
- aug2-firmware.bin
- aug2-common.xml
- aug2-00-87-12-aa-00-11.xml
List of Parameters
- Firmware/Configuration Update Enabled – enable automatic firmware/configuration updating from the TFTP/HTTP server.
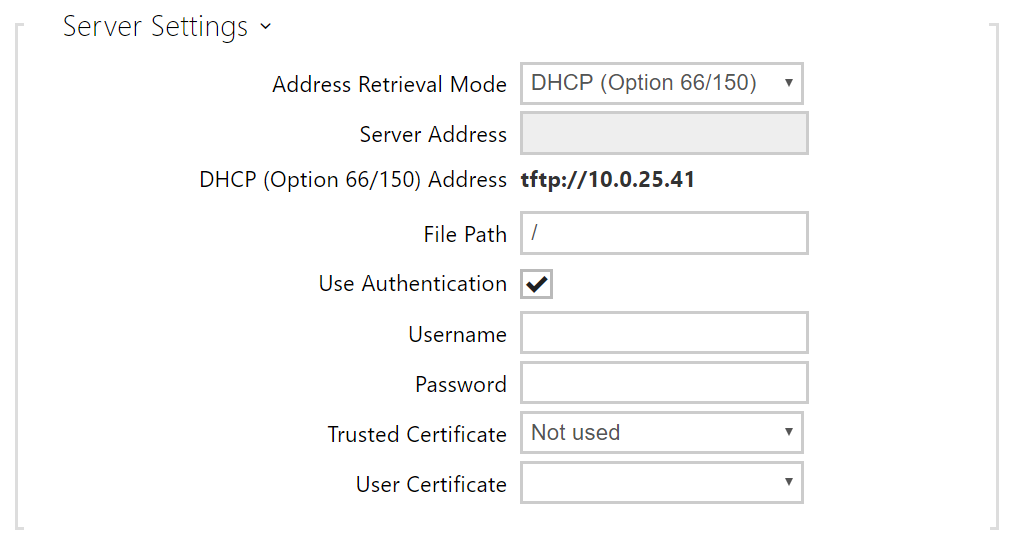
- Address Retrieval Mode – select whether the TFTP/HTTP server address shall be entered manually or a value retrieved automatically from the DHCP server using Option 66 shall be used.
- Server Address – enter the TFTP (tftp://ip_address), HTTP (http://ip_address) or HTTPS (https://ip_address) server address manually.
- DHCP (Option 66/150) Address – check the server address retrieved via the DHCP Option 66 or 150.
- File Path – set the path to firmware files folder. Enter / to search for model-firmware.bin (specific model) in the server's root folder. Refer to the sidebar (?) for details about models, etc.
- Use Authentication – enable authentication for HTTP server access.
- Username – enter the user name for server authentication.
- Password – enter the password for server authentication.
- Trusted Certificate – set the set of CA certificates for validation of the ACS public certificate.
- User Certificate – specify the user certificate and private key to validate the device right to communicate with the ACS.
- At Boot Time – enable check and/or execution of update upon every start.
- Update Period – set the update period. Set an automatic update to take place hourly/daily/weekly/monthly, or set the period manually.
- Update At – set the update time in the HH:MM format for periodical updating at a low-traffic time. The parameter is not applied if the update period is set to a value shorter than 1 day.
- Next Update At – display the next update time.
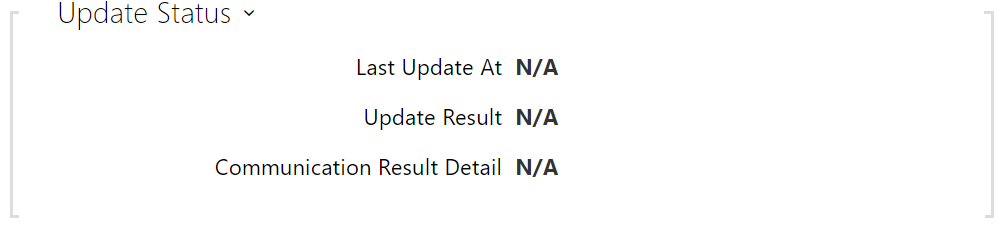
- Last Update At – last update time.
Update Result – last update result. The following options are available: DHCP option 66 failed, Firmware is up to date, Server connection failed, Running..., File not found.
- Communication Result Detail – server communication error code or TFTP/HTTP status code.
| Result | Description |
|---|---|
In progress ... | Update in progress |
Updated | The configuration/firmware update has been successful. With firmware update, the device will be restarted in a few seconds. |
| Firmware is up to date. | The firmware update attempt reveals that the latest firmware version has been loaded. |
DHCP Option 66 has failed. | The server address loading via DHCP Option 66 or 150 has failed. |
Invalid domain name | The server domain name is invalid due to wrong configuration or unavailability of the DNS server. |
Server Not Found | The requested HTTP/TFTP server fails to reply. |
Download failed | An unspecified error occurred during file download. |
File not found | The file has not been found on the server. |
File invalid | The file to be downloaded is corrupted or of a wrong type. |
Configuration
Use the Configuration tab to set automatic configuration download from the server defined by you. The 2N device periodically downloads a file from the server and gets reconfigured without getting restarted.
- Firmware update enabled – enable automatic firmware/configuration updating from the TFTP/HTTP server.
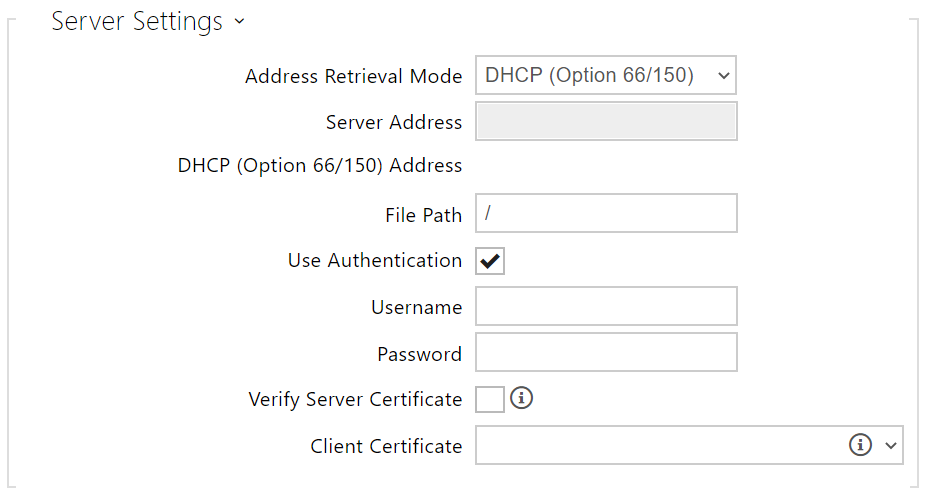
- Address Retrieval Mode – select whether the TFTP/HTTP server address shall be entered manually or a value retrieved automatically from the DHCP server using Option 66 shall be used.
- Server Address – enter the TFTP (tftp://ip_address), HTTP (http://ip_address) or HTTPS (https://ip_address) server address manually.
- DHCP (Option 66/150) Address – check the server address retrieved via the DHCP Option 66 or 150.
- File Path – set the firmware/configuration filename directory or prefix on the server. The device expects the XhipY_firmware.bin, XhipY-common.xml and XhipY-MACADDR.xml files, where X is the prefix specified herein and Y specifies the model.
- Use Authentication – enable authentication for HTTP server access.
- Username – enter the user name for server authentication.
- Password – enter the password for server authentication.
- Verify Server Certificate – set the set of CA certificates for validation of the ACS public certificate.
- Client Certificate – specify the client certificate and private key to validate the device right to communicate with the ACS.
Info
- The device contains the Factory Cert, a signed certificate used for British Telecom integration, for example.
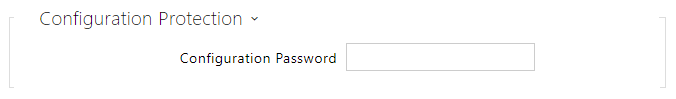
- Configuration Password – set password used to decrypt password-protected configuration.
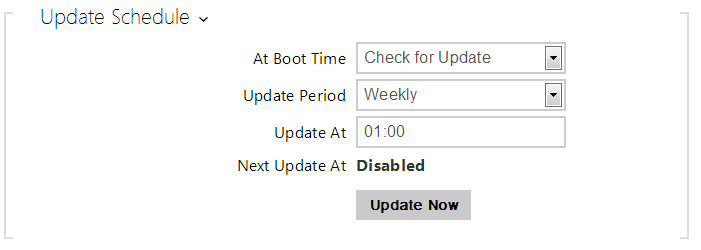
- At Boot Time – enable check and, if possible, update execution upon every device start.
- Update Period – set the update period. Set an automatic update to take place hourly/daily/weekly/monthly, or set the period manually.
- Update At – set the update time in the HH:MM format for periodical updating at a low-traffic time. The parameter is not applied if the update period is set to a value shorter than 1 day.
- Next Update At – set the next update time.
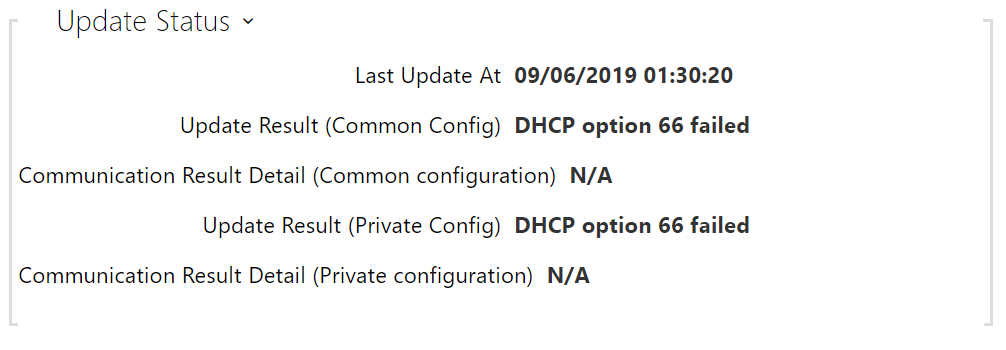
- Last Update At – last update time.
Update Result (Common Config) – last update result. The following options are available: DHCP option 66 failed, Firmware is up to date, Server connection failed, Running..., File not found.
- Communication Result Detail(Common Config) – server communication error code or TFTP/HTTP status code.
- Update Result (Private Config) – private configuration follows the common configuration update. The device with private configuration is identified by its MAC address. The following options are available: DHCP option 66 failed, Firmware is up to date, Server connection failed, Running..., File not found.
- Communication Result Detail (Private Config) – server communication error code or TFTP/HTTP status code.
My2N / TR069
Use this tab to enable and configure remote device management via the TR-069 protocol. TR-069 helps you reliably configure device parameters, update and back up configuration and/or upgrade device firmware.
The TR-069 protocol is utilised by the My2N cloud service. Make sure that TR-069 is enabled and Active profile set to My2N to make your device log in to My2N periodically for configuration.
This function helps you connect the device to your ACS (Auto Configuration Server). In this case, the connection to My2N will be disabled in the device.
- My2N / TR069 Enabled – enable connection to My2N or another ACS server.
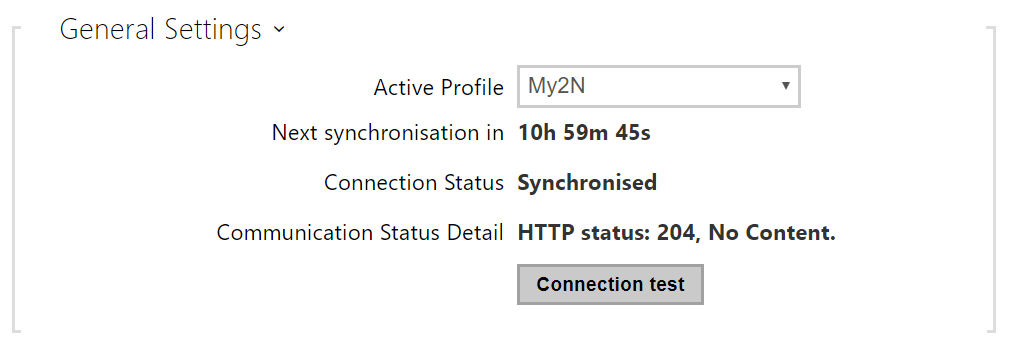
- Active Profile – select one of the pre-defined profiles (ACS), or choose a setting of your own and configure the ACS connection manually.
- Next Synchronisation in – display the time period in which the device shall contact a remote ACS.
- Connection Status – display the current ACS connection state or error state description if necessary.
- Communication Status Detail – server communication error code or HTTP status code.
- Connection test – test the TR069 connection according to the set profile, see the Active profile. The test result is displayed in the Connection status.
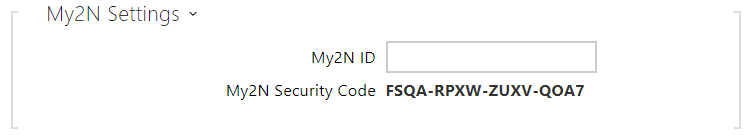
- My2N ID – unique identifier of the company created via the My2N portal.
- My2N Security Code – display the full application activating code.
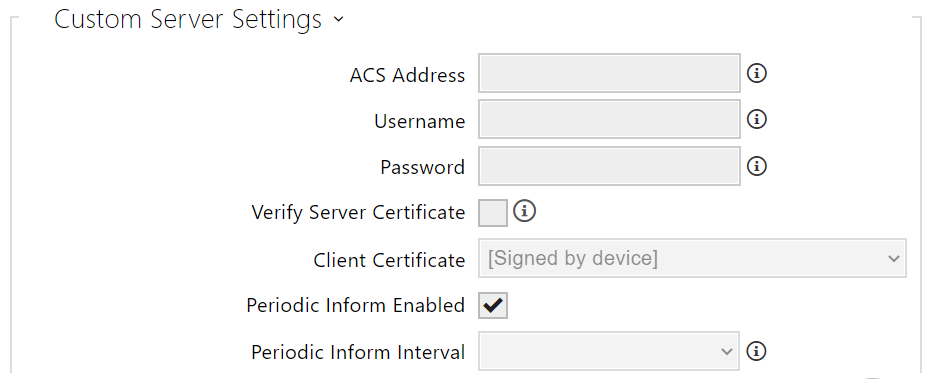
- ACS Address – set the ACS address in the following format: ipaddress[: port], 192.168.1.1:7547, for example.
- Username – set the user name for device authentication while connecting to the ACS server.
- Password – set the user password for device authentication while connecting to the ACS server.
- Verify Server Certificate – set the set of CA certificates for validation of the ACS public certificate. Choose one of three sets, see the Certificates subsection. If none is selected, the ACS public certificate is not validated.
- Client Certificate – specify the client certificate and private key to validate the device right to communicate with the ACS. Choose one of three sets, refer to the Certificates subsection.
- Periodic inform enabled – enable periodical logging of the device to the ACS.
- Periodic inform interval – set the interval of periodical logging of the device to the ACS if enabled by the Periodic inform enabled parameter.