5.2.1 Users
The User list contains up to 10 000 users – typically, each user is assigned just one position. The User list provides information on the users that are granted access to the building via the RFID cards.
If your external card reader is connected to the device via the Wiegand interface, the card ID is shortened to 6 or 8 characters for transmission (depending on the transmission parameters). If you apply a card to the reader, you will receive a complete ID, which is typically longer (8 chars or more). The last 6 or 8 characters, however, are identical. This is useful for comparing card IDs with the device database: if the IDs to be compared have different lengths, they are compared from the end and a match has to be found in 6 characters at least. If they have identical lengths, all the characters are compared. This ensures mutual compatibility of the internal and external readers.
All cards applied via the reader or the Wiegand interface are recorded. Refer to the Status > Access Log menu for the last 10 cards including the card ID/type, card tapping time and other information if necessary. With small systems, you can make a trick to enter card IDs: tap the card on the device reader and find it in the Access Log. Double-click to select the card ID and push CTRL+C. Now that you have the card ID in your box, you can insert it with CTRL+V in any settings field.
Having been read, the card ID is compared with the device card database. If the card ID matches any of the cards in the database, the appropriate action will be executed: switch activation (door unlocking, etc.). To change the switch number to be activated, use the Associated Switch parameter in the Hardware > Card Reader menu or the Associated Switch parameter in the Hardware > Modules menu of the card reader module.
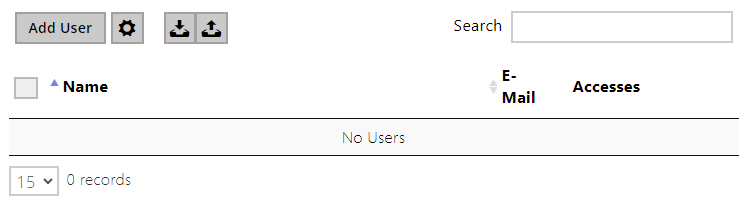
The Search in User list function works as a fulltext search in user names and e-mail addresses. It searches for all matches in the list. Press the button above the table to add a User. Click to show the user details. Click to set the table column display; the default table setting displays the user name, e-mail and assigned accesses. Pressto remove a user and delete its details. The icons in the access column describe the active user authentications.
Every record in the Users list includes the following parameters:
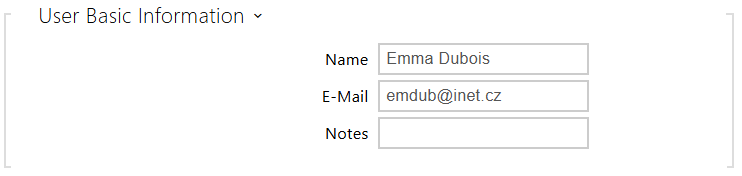
- Name – a mandatory parameter for easier user search, for example.
- E-mail – user e-mail address is used for sending information via email, e.g. about the user's access to the object or when using 2N Automation. You can enter more e-mail addresses separated with comma or semicolon.
Notes – is used for adding custom notes to a contact. It is possible to enter metadata into the note that is used for third-party system integrations. You can work with the content of the note in the Comparator block in Automation, see 2N Automation manual.
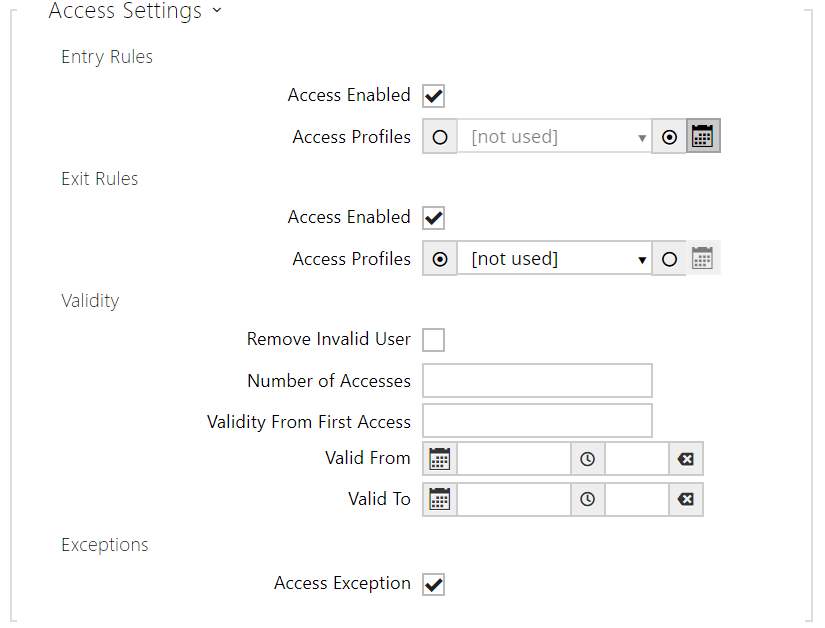
- Entry Rules
- Access Enabled – enable authentication via this access point.
- Access Profiles – select one of the profiles pre-defined in Directory > Time profiles or set the time profile for this element manually.
- Exit Rules
- Access Enabled – enable authentication via this access point.
- Access Profiles – select one of the profiles pre-defined in Directory > Time profiles or set the time profile for this element manually.
- Validity
- – set the time that the user will be valid for from the first successful authorization. Leave empty for no relative validity period. Relative validity may shorten the validity period but never extend it. The time is set in the format HH:MM, e.g., 06:09.
- Valid from – set the beginning of the mode validity term. Leave empty so that the start is not restricted. Valid From must precede Valid To.
- Valid to – set the end of the mode validity term. Leave empty so that the end is not restricted. Valid To must be after Valid From.
- Access Exception – enable this user to bypass Access Blocking and Anti-Passback rules.
Caution
- If the codes are identical with the codes already defined in the intercom configuration, the mark will appear at the colliding codes.
- The initial zeros are ignored as far as the code uniqueness is concerned. This means that two codes ONLY differing by the initial zero count are considered identical.
- PIN Code – set the user's Personal Identification Number. The code must include 2 characters at least.
- generates a QR code image. Codes shorter than 4 digits cannot be entered by QR code reading for security reasons. The codes must contain digits only. If authentication using a hexadecimal QR code is required, convert this code into the hexadecimal format before entering. Accepted hexadecimal range: 1000 to FFFFFFFF.
- Switch – set a private user switch activation code: up to 16 characters including digits 0–9 only. The code must include at least two door unlocking characters via the device keypad and at least one door unlocking character via DTMF.
- generates a QR code image. Codes shorter than 4 digits cannot be entered by QR code reading for security reasons. The codes must contain digits only. If authentication using a hexadecimal QR code is required, convert this code into the hexadecimal format before entering. Accepted hexadecimal range: 1000 to FFFFFFFF.
- Card ID – set the user access card ID: 6–32 characters including 0–9, A–F. Each user can be assigned up to two access cards. When a valid card is tapped on the reader, the switch associated with the card reader gets activated. If the double authentication mode is enabled, the switch can only be activated using both a card and numeric code.
- Virtual card ID – set the user virtual card ID for user identification in the devices that are integrated with the 2N device via a Wiegand interface. Each user can be assigned just one virtual card. The virtual card ID is a sequence of 6–32 characters: 0–9, A–F. After the user is validated via the Bluetooth/biometric reader, the identifier is sent to the device integrated with the 2N device via Wiegand. After the user is validated via the Bluetooth or Biometric Reader, the virtual card ID is sent to the Wiegand interface if the configuration (Services > Access Control) is set to send IDs to Wiegand.
- Auth ID – unique WaveKey ID for access control. It's saved to the mobile device during the pairing process. The Auth ID consists of 32 hexadecimal characters.
- pair via USB reader
- pair via this device
- delete Auth ID
Pairing State – display the current pairing state (Inactive, Waiting for pairing, PIN validity expired, Paired, Too many attempts).
Note
- After 10 unsuccessful pairing attempts, a 30 s pause is activated automatically for security reasons, during which it is impossible to make any further pairing attempts.
- Valid Until – date and time at which the authorization PIN validity expires or the temporary pairing suspension ends.
Pairing via Bluetooth Module in Device
To pair a mobile phone with the user:
- Click at Auth ID to start pairing for the selected user account.
- A dialogue window with the PIN code is displayed.
- Find the appropriate reader in the My2N application and press Start pairing.
- Enter the code from item 2 into the input field.
- Pairing is completed.
- User Fingerprints – display the set count of fingerprints; up to 2 different fingerprints can be set. This section is displayed only if the biometric reader module is available.
- enrol via USB reader
- enrol via Fingerprint scanner module 3
Caution
- The fingerprint loading capacity is up to 2000 per device.
Refer to Subs. 5.2.1.1 Pokyny pro nastavení uživatelských otisků prstů for user fingerprint loading details.
In case the function is on, the event is recorded into the LicensePlateRecognized history when a valid HTTP request has been received.
If an image is sent within the HTTP request (photo part or whole photo of the license plate detecting scene), it is saved. The last five photos are stored in the device memory and can be retrieved via an HTTP request sent to api/lpr/image available in 2N Access Commander.
It is advisable that each license plate should be assigned to just one entry in the directory. Multiple license plate assignments may result in the inability to assign a license plate to an entry in the directory unambiguously (the first entry assigned the specified license plate is selected and given the access rights).
- License Plates – set the car license plates for the selected record in the directory. A record can be assigned multiple license plates separated with commas (up to 20). The set license plates are used for recognizing license plates from external camera images (refer to the Interoperability manual for details). One license plate may include up to 10 characters. The set string length is limited to 255 characters.
- Floors – select the floors available to the user.
- Time Profile – select one or more time profiles to be applied. Set the time profiles in the Directory > Time Profiles section.
- mark the selection from predefined profiles or manual setting of a time profile for the given element.
- set a time profile for the given element.